A brief field guide to the internet’s tools for repression
By Callum Tennent | October 22, 2019
 Girl protests against Russian domestic control of the internet with a sign that reads “You will not switch us off the internet.” March 10th, 2019. Credit: Elena Rostunova, Shutterstock.
Girl protests against Russian domestic control of the internet with a sign that reads “You will not switch us off the internet.” March 10th, 2019. Credit: Elena Rostunova, Shutterstock.
Autocratic governments increasingly use technology to carry out mass surveillance and censorship. As their methods have gained popularity, the technology that facilitates them has become cheaper, more accessible, and easier to purchase in the marketplace. Consequently, those living under repressive regimes of any size are at greater risk of censorship and surveillance systems that monitor their every move. Ironically, the tools and practices that originally supported free speech and the sharing of information can now be manipulated to repress dissent.
And governments are not the only threats to consider: US President Donald Trump signed a bill that allows internet service providers to sell data about their users and their online activities to anyone interested. The Electronic Frontier Foundation says this action ends a “decades-long legal tradition that your communications provider is never allowed to monetize your personal information without asking for your permission first.”
The variety and extent of the tools and tactics use to monitor a user’s activities can be bewildering. So, here’s a quick technical rundown of some of the most prevalent and most nasty ones, and how they infringe on human rights. (Think of this as a sort of field guide to the internet’s tools for repression; it is by no means an exhaustive encyclopedia.) There are four major categories: commonplace tactics for censorship and surveillance; widely available surveillance tools in the commercial marketplace; tactics influenced by the rise of the sovereign internet; and technologies based upon the model of the Trojan horse.
Censorship and surveillance tactics. Unfortunately, there are a number of ways that governments and others can monitor and interrupt a user’s internet activity. Internet service provider filtering is just one method used by authorities to censor sites. It involves the service provider manually blocking or monitoring a user’s access to blacklisted sites—although this can be readily circumvented by using a proxy (a computer on the web that redirects your web browsing activity) or a virtual private network, which is a piece of software that keeps your internet activity private and secure by building an encrypted tunnel between your traffic and those trying to spy on you. Wirecutter, PC Mag, and the digital privacy research group that I work for, Top10VPN, have done reviews of the various offerings by makers of virtual private network software. And it should be noted that just like any other technology, this software tool to get around manual blocking and monitoring has its pros and cons, as can be seen by the headline of a New York Times article on the subject: “For Internet Privacy, VPNs Are an Imperfect Shield.”
A more invasive way of blocking content and spying on users is deep packet inspection. This is a type of data processing that allows internet service providers to see detailed information on what sites users are attempting to access. Internet service providers do this by opening up the so-called packets of data sent by a user before they reach their destination, much like a letter being opened in a postal depot. Data can then be re-routed or dumped entirely.
Deep packet inspection is a method authorities use in China to censor the internet, by scanning data packets for certain keywords or banned sites and re-routing data accordingly, preventing users from accessing content unapproved by the Chinese Communist Party.
Another method, known as Border Gateway Protocol traffic highjacking, also enables internet monitoring and site blocking. It does this by abusing the trust-based nature of the system for efficiently routing data between independently operated networks of autonomous systems—which are collections of internet addresses operated by the same network operator.
Because this protocol directs data packets towards their destination, malicious actors can manipulate a Border Gateway Protocol to reroute traffic, intercept data, or modify it. In April 2018, Border Gateway Protocol hijacking was used to reroute Amazon traffic in an attempt to access crypto-currency wallets.
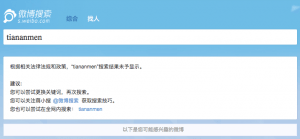
Another approach that autocracies favor: Preventing users from accessing blacklisted sites at all. Countries like China use a version of this technique, known as “Domain Name System cache poisoning,” to prevent users from accessing blacklisted sites. When running correctly, the Domain Name System matches the name of the site a user is attempting to access with its corresponding Internet Protocol (IP) address. Domain Name System cache poisoning prevents users from reaching the site by matching them to the wrong IP address, routing them to the incorrect destination. Alternatively, they are blocked entirely. To give one simple example, when users in China type any combination of words such as “Tiananmen Square massacre,” “June 4,” “1989,” or “tank man,” into Weibo—the leading Chinese microblogging platform—they get a message that reads “According to the relevant laws and regulations, search results for [this phrase] cannot be displayed.” Even the most mundane of phrases can be blocked, such as combination of numbers that refer to the day of June 4 and the year 1989.
The commercialization of surveillance technology. Although larger autocratic regimes commonly use surveillance and censorship technology and techniques, it’s worrying that less-powerful governments increasingly use widely available, off-the-shelf commercial surveillance and censorship software.
While authorities often claim commercial surveillance software is used to protect national security, it’s also often used to monitor dissidents or ordinary civilians. NSO Group Technologies is a private software company that makes such products; Saudi Arabian authorities used NSO software to spy on journalist Jamal Khashoggi before his murder. In Panama—a country guilty of human rights violations—NSO technology has been used for wiretapping Americans.
Commercial surveillance software arms governments that would otherwise lack the technical know-how and ability with the tools to easily surveil and censor citizens. Earlier in the year, the United Nations called for a moratorium on surveillance technology as a result of the technology’s involvement in governmental human rights abuses.
Rise of the sovereign internet. The concept of a domestically controlled internet is becoming more and more popular with repressive regimes, largely due to the success of China’s Great Firewall. China has begun to export surveillance technology to other countries, such as the Philippines and Kenya, as part of their so-called Belt and Road foreign infrastructure initiative, involving the creation of a vast, $1.3 trillion network of railways, energy pipelines, highways, and border crossings that seeks to create a China-led trading bloc involving two-thirds of the world’s population.
Taking a page from China’s experience, Russia has committed to setting up its own “sovereign internet”—in which a country controls and creates boundaries around its internet infrastructure—and has even gone so far as to solidify its plans for a domestic internet with what it calls sovereign internet legislation. Russia has banned virtual private networks and encrypted services like Telegram, and carries out mass surveillance using Russian-made “SORM” hardware wiretaps that all Russian internet service providers—and mobile telecommunications firms—are required by law to install in their data centers. (The acronym stands for “System for Operative Investigative Activities,” or “SORM” in Russian, and it allows Russian police and other law enforcement agencies to connect to devices, set up logging and filtering rules, and retrieve logged data later.) With such equipment, mass surveillance can be carried out—even including web addresses and phone numbers.
Trojan horse technology. With censorship circumvention tools gaining popularity, it’s no wonder governments have decided to block or restrict their use. Virtual Private Networks are now banned in Belarus and Turkmenistan, while other countries like the United Arab Emirates only allow the use of state-sanctioned versions.
Some governments are attempting to exploit the popularity of these products to increase their reach of surveillance. By being involved in the production of tools like virtual private networks, or making it a legal requirement for these services to hand over user information to authorities, governments can gain direct access to a user’s internet behavior.
Russian authorities have banned all virtual private networks that have refused to censor sites on the country’s blacklist. Kaspersky’s VPN is the only major player that chose to comply, which means that any users of their virtual private network will be unable to access blocked sites and will likely have their activity logged and monitored by Russian authorities.
Any censorship circumvention tool that has government involvement can be viewed as a Trojan horse, masquerading as a tool to protect the user when in reality it puts users in more danger.
Our Freedoms at Risk. If nothing is done to stop the spread of the dangerous technologies I’ve described, excessive levels of surveillance and censorship that drastically infringe on users’ rights will become the norm. Democratic countries must take a stand, implementing trade sanctions and publicly condemning governments that carry out these practices. Private companies that profit from these technologies must also be regulated, so that their products cannot continue to be used to undermine democracy.
Together, we make the world safer.
The Bulletin elevates expert voices above the noise. But as an independent nonprofit organization, our operations depend on the support of readers like you. Help us continue to deliver quality journalism that holds leaders accountable. Your support of our work at any level is important. In return, we promise our coverage will be understandable, influential, vigilant, solution-oriented, and fair-minded. Together we can make a difference.
Keywords: Censorship, Internet, Trojan Horse, surveillance state
Topics: Disruptive Technologies