Keeping classified information secret in a world of quantum computing
By Jake Tibbetts | February 11, 2020
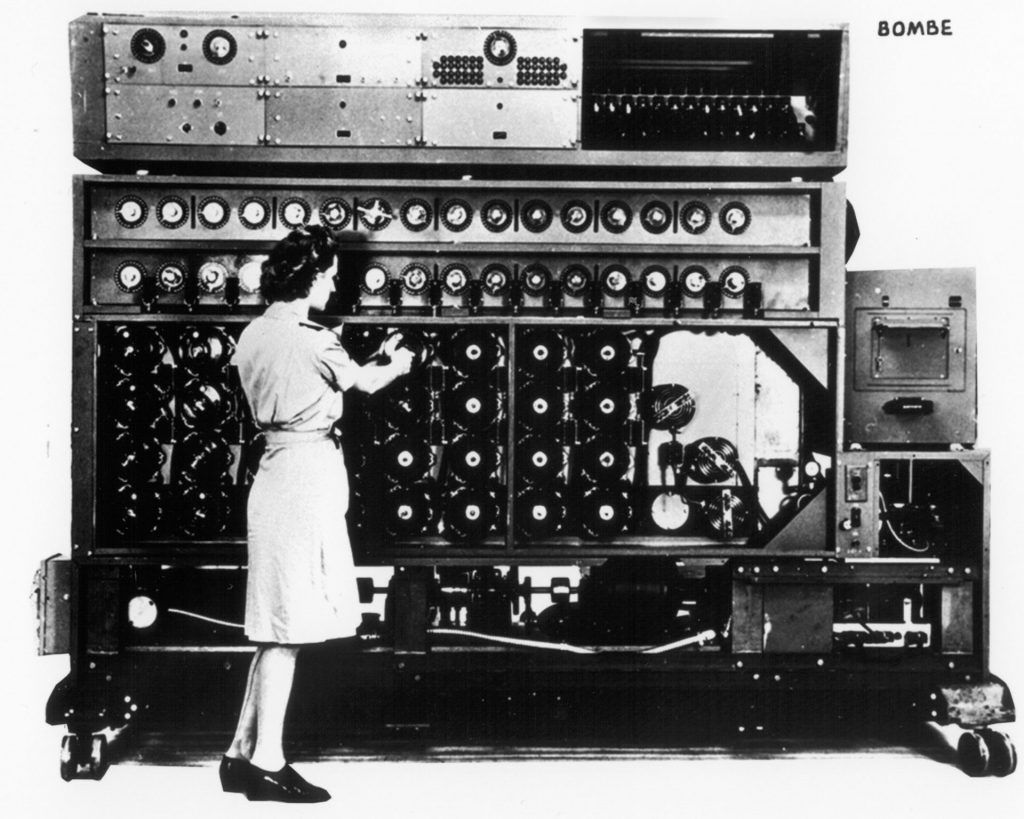 By the end of 1943, the US Navy had installed 120 electromechanical Bombe machines like the one above, which were used to decipher secret messages encrypted by German Enigma machines, including messages from German U-boats. Built for the Navy by the Dayton company National Cash Register, the US Bombe was an improved version of the British Bombe, which was itself based on a Polish design. Credit: National Security Agency
By the end of 1943, the US Navy had installed 120 electromechanical Bombe machines like the one above, which were used to decipher secret messages encrypted by German Enigma machines, including messages from German U-boats. Built for the Navy by the Dayton company National Cash Register, the US Bombe was an improved version of the British Bombe, which was itself based on a Polish design. Credit: National Security Agency
Quantum computing is a technology that promises to revolutionize computing by speeding up key computing tasks in areas such as machine learning and solving otherwise intractable problems. Some influential American policy makers, scholars, and analysts are extremely concerned about the effects quantum computing will have on national security. Similar to the way space technology was viewed in the context of the US-Soviet rivalry during the Cold War, scientific advancement in quantum computing is seen as a race with significant national security consequences, particularly in the emerging US-China rivalry. Analysts such as Elsa Kania have written that the winner of this race will be able to overcome all cryptographic efforts and gain access to the state secrets of the losing government. Additionally, the winner will be able to protect its own secrets with a higher level of security than contemporary cryptography guarantees.
These claims are considerably overstated. Instead of worrying about winning the quantum supremacy race against China, policy makers and scholars should shift their focus to a more urgent national security problem: How to maintain the long-term security of secret information secured by existing cryptographic protections, which will fail against an attack by a future quantum computer.
The race for quantum supremacy. Quantum supremacy is an artificial scientific goal—one that Google claims to have recently achieved—that marks the moment a quantum computer computes an answer to a well-defined problem more efficiently than a classical computer. Quantum supremacy is possible because quantum computers replace classical bits—representing either a 0 or a 1—with qubits that use the quantum principles of superposition and entanglement to do some types of computations an order of magnitude more efficiently than a classical computer. While quantum supremacy is largely meant as a scientific benchmark, some analysts have co-opted the term and set it as a national-security goal for the United States.
These analysts draw a parallel between achieving quantum supremacy and the historical competition for supremacy in space and missile technology between the United States and the Soviet Union. As with the widely shared assessment in the 1950s and 1960s that the United States was playing catchup, Foreign Policy has reported on a “quantum gap” between the United States and China that gives China a “first mover advantage.” US policy experts such as Kania, John Costello, and Congressman Will Hurd (R-TX) fear that if China achieves quantum supremacy first, that will have a direct negative impact on US national security.
Some analysts who have reviewed technical literature have found that quantum computers will be able to run algorithms that allow for the decryption of encrypted messages without access to a decryption key. If encryption schemes can be broken, message senders will be exposed to significant strategic and security risks, and adversaries may be able to read US military communications, diplomatic cables, and other sensitive information. Some of the policy discussion around this issue is influenced by suggestions that the United States could itself become the victim of a fait accompli in code-breaking after quantum supremacy is achieved by an adversary such as China. Such an advantage would be similar to the Allies’ advantage in World War II when they were able to decrypt German radio traffic in near-real time using US and British Bombe machines (see photo above).
The analysts who have reviewed the technical literature have also found that quantum technologies will enable the use of cryptographic schemes that do not rely on mathematical assumptions, specifically a scheme called quantum key distribution. This has led to the notion in the policy community that quantum communications will be significantly more secure than classical cryptography. Computer scientist James Kurose of the National Science Foundation has presented this view before the US Congress, for example.
Inconsistencies between policy concerns and technical realities. It is true that quantum computing threatens the viability of current encryption systems, but that does not mean quantum computing will make the concept of encryption obsolete. There are solutions to this impending problem. In fact, there is an entire movement in the field to investigate post-quantum cryptography. The aims of this movement are to find efficient encryption schemes to replace current methods with new, quantum-secure encryption.
The National Institute of Standards and Technology is currently in the process of standardizing a quantum-safe public key encryption system that is expected to be completed by 2024 at the latest. The National Security Agency has followed suit by announcing its Commercial National Security Algorithm Encryption Suite. These new algorithms can run on a classical computer—a computer found in any home or office today. In the future, there will be encryption schemes that provide the same level of security against both quantum and classical computers as the level provided by current encryption schemes against classical computers only.
Because quantum key distribution enables senders and receivers to detect eavesdroppers, analysts have claimed that the ability of “the recipient and sender [to] determine if the message has been intercepted” is a “major advantage” over classical cryptography. While eavesdropper detection is an advancement in technology, it does not actually provide any significant advantage over classical cryptography, because eavesdropper detection is not a problem in secure communications in the first place.
When communicating parties use quantum key distribution, an eavesdropper cannot get ciphertext (encrypted text) and therefore cannot get any corresponding plaintext (unencrypted text). When the communicating parties use classical cryptography, the eavesdropper can get ciphertext but cannot decrypt it, so the level of security provided to the communicating parties is indistinguishable from quantum key distribution.
The more pressing national security problem. While the technical realities of quantum computing demonstrate that there are no permanent security implications of quantum computing, there is a notable longer-term national security problem: Classified information with long-term intelligence value that is secured by contemporary encryption schemes can be compromised in the future by a quantum computer.
The most important aspect of the executive order that gives the US government the power to classify information, as it relates to the discussion of quantum computing and cryptography, is that this order allows for the classification of all types of information for as long as 25 years. Similarly, the National Security Agency provides guidelines to its contractors that classified information has a potential “intelligence life” of up to 30 years. This means that classified information currently being secured by contemporary encryption schemes could be relevant to national security through at least 2049—and will not be secure in the future against cryptanalysis enabled by a quantum computer.
In the past, the United States has intercepted and stored encrypted information for later cryptanalysis. Toward the end of World War II, for example, the United States became suspicious of Soviet intentions and began to intercept encrypted Soviet messages. Because of operator error, some of the messages were partially decryptable. When the United States realized this, the government began a program called the Venona Project to decrypt these messages.
It is likely that both the United States and its adversaries will have Venona-style projects in the future. A few scholars and individuals in the policy community have recognized this problem. Security experts Richard Clarke and Robert Knake have stated that “governments have been rumored for years to be collecting and storing other nations’ encrypted messages that they now cannot crack,” with the hope of cracking them in the future with a quantum computer.
As long as the United States continues to use encryption algorithms that are not quantum-resistant, sensitive information will be exposed to this long-term risk. The National Institute of Standards and Technology’s quantum-resistant algorithm might not be completed—and reflected in the National Security Agency’s own standard—until 2024. The National Security Agency has stated that “algorithms often require 20 years to be fully deployed on NSS [National Security Systems].” Because of this, some parts of the US national security apparatus may be using encryption algorithms that are not quantum-resistant as late as 2044. Any information secured by these algorithms is at risk of long-term decryption by US adversaries.
Recommendations for securing information. While the United States cannot take back any encrypted data already in the possession of adversaries, short-term reforms can reduce the security impacts of this reality. Taking 20 years to fully deploy any cryptographic algorithm should be considered unacceptable in light of the threat to long-lived classified information. The amount of time to fully deploy a cryptographic algorithm should be lowered to the smallest time frame feasible. Even if this time period cannot be significantly reduced, the National Security Agency should take steps to triage modernization efforts and ensure that the most sensitive systems and information are updated first.
Luckily for the defenders of classified information, existing encryption isn’t completely defenseless against quantum computing. While attackers with quantum computers could break a significant number of classical encryption schemes, it still may take an extremely large amount of time and resources to carry out such attacks. While the encryption schemes being used today can eventually be broken, risk mitigation efforts can increase the time it takes to decrypt information.
This can be done by setting up honeypots—systems disguised as vulnerable classified networks that contain useless encrypted data—and allowing them to be attacked by US adversaries. This would force adversaries to waste substantial amounts of time and valuable computer resources decrypting useless information. Such an operation is known as as defense by deception, a well-proven strategy to stymie hackers looking to steal sensitive information. This strategy is simply an application of an old risk mitigation strategy to deal with a new problem.
Quantum computing will have an impact on national security, just not in the way that some of the policy community claims that it will. Quantum computing will not significantly reduce or enhance the inherent utility of cryptography, and the outcome of the race for quantum supremacy will not fundamentally change the distribution of military and intelligence advantages between the great powers.
Still, the United States needs to be wary of long-term threats to the secrecy of sensitive information. These threats can be mitigated by reducing the deployment timeline for new encryption schemes to something significantly less than 20 years, triaging cryptographic updates to systems that communicate and store sensitive and classified information, and taking countermeasures that significantly increase the amount of time and resources it takes for adversaries to exploit stolen encrypted information. The threats of quantum computing are manageable, as long as the US government implements these common-sense reforms.
Editor’s Note: The author wrote a longer version of this essay under a Lawrence Livermore National Laboratory contract with the US Energy Department. Lawrence Livermore National Laboratory is operated by Lawrence Livermore National Security, LLC, for the US Department of Energy, National Nuclear Security Administration under Contract DE-AC52-07NA27344. The views and opinions of author expressed herein do not necessarily state or reflect those of the United States government or Lawrence Livermore National Security, LLC. LLNL-JRNL-799938.
Together, we make the world safer.
The Bulletin elevates expert voices above the noise. But as an independent nonprofit organization, our operations depend on the support of readers like you. Help us continue to deliver quality journalism that holds leaders accountable. Your support of our work at any level is important. In return, we promise our coverage will be understandable, influential, vigilant, solution-oriented, and fair-minded. Together we can make a difference.